The short answer is this: a firewall intercepts all communications between you and the internet and decides if the information is allowed to pass.
Covered in this article:
- The Long Answer
- Hardware Firewalls vs Software Firewalls
- What does a firewall protect me from?
- What can get through?
- How different is a firewall from what a NAT router does?
- How can I tell that my firewall is working?
- Does a firewall filter internet content?
- Can a firewall protect my kids from the internet?
- Does a firewall block spam?
- What are the adverse effects of running a firewall?
- What else should I do to protect my network?
The Long Answer:
Now we can address the long answer. Let's forget for now the fact that a firewall can be either hardware or software; they both have a similar function. We'll talk about the differences between hardware and software a lit bit later.
When your computer is connected to the internet, information flows both into and out of it. For instance, when you surf the web, you send out a request for a web page, and you get back in the page you asked for. When you check your email you send out a request for your email, and you get back in your email messages. Just about every communication on the internet is bi-directional, or two-way.
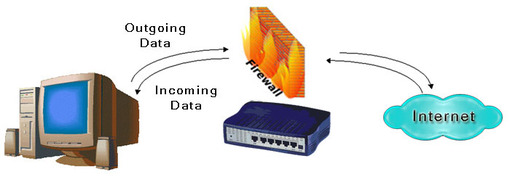
It is important to note that firewalls are aware of connections. A connection exists between you and your email server when you check your email, and one exists between you and a web server when you browse the web. This connection is what data flows over. Firewalls are aware of connections. When we talk about an in rule or an out rule, we are referring to the direction the connection was created. So when you check your email, you are creating a connection out to your mail server. This requires an out rule in your firewall. When the email server sends data back to you in the connection that you have already created, you do not need an in rule because the connection has already been created.
Most firewalls, by default, will block all traffic both in and out. This is what we call Deny all by default. In this state, it is as if your computer is not even connected to the Internet. While this is a very safe state to be in, it is not very useful. So we have to create a set of rules to tell the firewall what we consider safe and ok. Everything else is by default considered not safe.
Most programs that we want to talk on the internet with are harmless, and simply request data that we want with information that we consider not private. For these programs, we want a firewall to be completely transparent. In other words, you want to be able to surf the web and check your email even if you have a firewall installed. In order for these programs to be able to work, we have to create an allow rule and we set it to allow both in and out traffic.
As you create rules to allow traffic in and out, you are creating tiny holes in your firewall for the traffic to flow through. That is why many internet users call creating rules pin-holing your firewall. The more pinholes you create in your firewall, the less secure your network becomes, so you should only create as many pinholes or rules as you need to use the internet to do what you want to do.
Hardware Firewalls vs. Software Firewalls
Hardware Firewalls
Hardware Firewalls are usually a router or other similar device. Many modern routers have a firewall built into them. To use the firewall, you must log in to your router, usually from inside your network. You can not log in from the Internet by default, this would break the security of the firewall. Once you are logged in to your router, you can find the firewall section and begin creating rules.
Hardware Firewalls are exceptional at blocking intruders and attacks from the internet and from inside your network. The downside to hardware firewalls is that they are a little more difficult to configure. You have to know the port numbers that you want to block or allow. These can be very difficult to find. We have a large database of port numbers that you can view. However, once you get a hardware firewall set up, it is the most secure and fastest option out there. In addition, one hardware firewall protects your entire network, so the overall cost is usually lower if you have more than one computer.
Software Firewalls
Software firewalls are applications that you install on each PC on your network. These may be the best option for users who only have 1 computer on their network. They work by allowing programs to communicate on the internet by program name instead of by port number. Most of them do offer firewalling by port number, but the default behavior is usually to firewall by program name.
Firewalling by program name means allowing a certain application unlimited access to the internet. For instance, if you trust Firefox then you add it to your list of allowed applications in your software firewall. Now you can surf the web using Firefox. If you want to add more security, you may decide to block the other browsers on your computer, forcing all users to use Firefox.
The disadvantage of software firewalls is multifaceted. First, you have to purchase a copy for every PC on your network. This can get expensive and can be a maintenance issue. Second, they can impair the functionality of your computer. Some firewalls are just difficult to configure, and until you configure them correctly, you may not be able to surf the web or check your email. This makes it very difficult to get help.
The biggest problem with software firewalls comes is that they trust applications completely. Once you have told your software firewall that you trust Firefox, Firefox can now do anything it wants to on the internet. By default, Firefox is a safe program, but there may be some malware out there that will take advantage of it and use it to do their dirty work. Since you have told your software firewall that you trust Firefox, this malware now has the ability to do anything it wants on the internet as if your firewall was never there. Therefore, software firewalls must be coupled with good antivirus and malware protection.

What does a firewall protect me from?
Firewalls, in general, protect you from malicious Internet attacks. These attacks can come from the outside or the inside. Outside attacks are people trying to get into your network so that they can take control of your computers, or use your computers to do things on the internet. Inside attacks are software that has already been installed on your computer trying to connect out to the internet, usually to get instructions from an internet hacker. By blocking both incoming and outgoing traffic, a firewall protects you from both of these kinds of attacks.
What can get through?
Generally, anything that really wants to. If you run a software firewall and allow an application to communicate on the internet, then a malicious piece of software may be able to piggyback some communications on top of that application. Of course, the malicious software author would have to account for this when they write the malware. This is currently rare making software firewalls pretty effective. If you run a hardware firewall and open up some ports, then any application that wants to can communicate on those ports. The application author would have to predefine that these open ports should be used, which keeps the odds of this happening pretty low.
The important thing to note is that a firewall is not a 100% solution to protecting your computer or network. Security needs to be a holistic approach, and the firewall is simply one aspect of many different things that should be done to keep your network safe.
How different is a firewall from what a NAT router does?
A NAT (Network Address Translation) router is sometimes called a firewall. The truth is, it is less than a firewall in many ways. NAT routers only block traffic in one direction; they only block incoming traffic. Firewalls block both directions.
While NAT is an effective barrier against people who want to get into your network, it provides few options to configure it. Most NATs do not allow you to create rules based on complex criteria such as time of day, source address, destination address, traffic direction, and others.
How can I tell that my firewall is working?
You should test your firewall.
To test your firewall for outgoing functionality, remove the rules for a program such as Firefox and try to surf the web. You should not be able to surf. If you can surf, then your firewall is not blocking outgoing traffic.
Does a firewall filter internet content?
No, most firewalls do not filter the content of the internet. Their functionality is indiscriminate of the content that is being downloaded. They only block certain applications or certain ports, not certain topics.
Can a firewall protect my kids from the internet?
No, if you want to protect your kids from online predators, scams, phishing, and cyberstalking you need to use other programs. A firewall only blocks certain applications and ports.

Does a firewall block spam?
No, a firewall does not block spam. When you install a firewall, you usually configure it to allow your email program to download your email messages. Spam, or unwanted email, is downloaded by your email program with your other messages. The firewall has no ability to block spam.
What are the adverse effects of running a firewall?
Some applications will not work very well behind a firewall. Many games need lots of ports open to the internet to function. Streaming video and audio may be affected, as well as Peer to Peer (P2P) applications such as uTorrent, Kazaa, WinMX, Azureus, and BitTorrent. Voice over IP (VOIP) may be affected as well.
In addition, some software firewalls may significantly slow down your computer or even cause it to stop working entirely. A software firewall is a very involved piece of software and it integrates very deeply into the operating system. You should probably back up your personal data files before installing one.
What else should I do to protect my network?
- If you have a wireless network, you should follow our guides about securing it. Open wireless networks are a huge security risk for your computer.
- Keep your computer up to date by using the Windows Update feature built into modern versions of Windows.
- Run AntiVirus software with * real-time protection*. The different virus scanners may call this something different from vendor to vendor, but the general concept is the same: you want some type of software running that is always scanning your computer for malware or virus activity.
- Only forward as many ports as you need to.
- Do not keep your sensitive passwords in a file on your computer. If someone hacks into your computer, they will gain access to all of your sensitive data. Passwords should be written on paper in your office.








